Have you ever released a shiny new API, only to get an avalanche of complaints because your mobile app (or a partner integration) suddenly broke? I’ve been there—pacing around the office, coffee in hand, fielding frantic Slack pings: “The checkout endpoint changed again?” That’s why API gateways and backward compatibility aren’t just buzzwords; they’re your safety net in a fast-moving microservices world. Let’s unpack how gateways help you manage, secure, and version your APIs, and how you can evolve without leaving clients stranded in the dust.
Why API Gateways and Backward Compatibility Matter
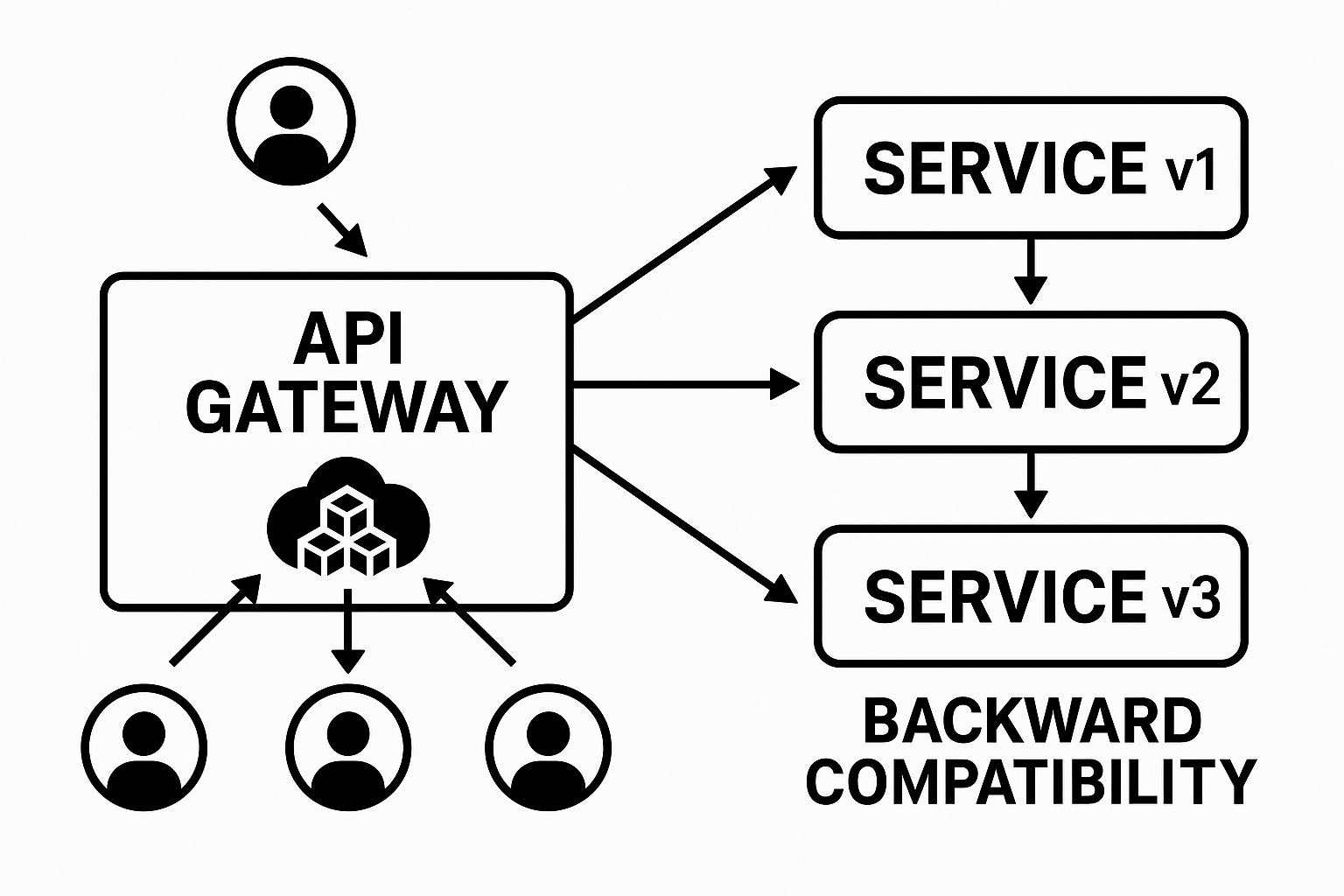
At its core, an API gateway sits between clients and your microservices, acting as a reverse proxy that routes requests, enforces security policies, transforms payloads, and handles cross- cutting concerns like rate limiting and caching. Instead of each service reinventing authentication or request throttling, you centralize those features in one place. Now imagine rolling out a new version of your user service that renames username to user_name in the JSON response. Without backward compatibility, every client that parsed username would crash. A gateway lets you map old fields to new ones—silently translating between the versions—so your next-gen features roll out smoothly while legacy clients keep humming along.
Practical Steps & Anecdotes
Step 1: Choose Your Gateway
Whether it’s Kong, Ambassador, AWS API Gateway, or an NGINX-based proxy, pick a tool that fits your stack. Our team started with a simple NGINX ingress in Kubernetes—lightweight and familiar. Later, we migrated to Kong because we needed a plugin ecosystem for JWT validation and sophisticated traffic routing.
Anecdote: On day one, we forgot to enable CORS in our gateway. Our front-end team spent half a day troubleshooting fetch errors before we realized the gateway was silently dropping OPTIONS requests. Rookie mistake—now every new gateway config includes a CORS sanity check in our deployment pipeline.
Step 2: Define Versioning Strategy
URI Versioning: /v1/orders, /v2/orders. Simple and explicit, but can clutter your routes.
Header Versioning: Clients send Accept: application/vnd.myapp.v2+json. Cleaner URLs, but adds complexity in client code.
Query Parameter Versioning: /orders?version=2. Easy to implement, but less discoverable.
We opted for URI versioning at first—clients found it easier to test with explicit routes. Later, as our API surface grew, we switched to header-based versioning to keep URLs tidy.
Step 3: Schema Mapping and Transformation
Use your gateway’s transformation plugins or write Lua/Vue scripts to rename fields, drop deprecated properties, or even split a single request into multiple upstream calls. When our billing service replaced totalAmount with amount and currency, we added a transformation rule in the gateway: map amount → totalAmount for any legacy client hitting /v1/orders. That bit of glue kept our partner integrations running while we updated their code on a separate timeline.
Step 4: Testing and Monitoring
Create integration tests that hit both v1 and v2 endpoints, verifying the gateway’s transformations. We hooked our CI pipeline to spin up a local Kong container and run Postman collections against it. Plus, set up metrics to track calls by version—if you see v1 traffic suddenly spike, it might indicate a new client hasn’t upgraded yet.
Overcoming Common Hurdles
Configuration Sprawl: Gateways can become a hairball of plugins and Counteract this by storing configs in version control (e.g., declarative YAML for Kong) and automating deployments.
Performance Overhead: Each transformation or plugin adds latency. Benchmark your gateway under load and optimize or cache hot We shaved off 20 ms per request by moving authorization checks to a lightweight Lambda authorizer instead of running a full Lua script.
Breaking Changes Leakage: Even with transformations, some changes—like altering authentication flows—can’t be masked. Always maintain clear deprecation policies: announce retiring of v1 six months in advance, provide migration guides, and send automated deprecation headers in responses.
Security Blind Spots: Centralizing auth in the gateway is great, but it also becomes a single point of Harden your gateway with strict network policies, mutual TLS, and regular security audits.
Conclusion
API gateways are your Swiss Army knife for managing microservices: they route traffic, enforce policies, and—most importantly—help you preserve backward compatibility so you can innovate fearlessly. By choosing a versioning strategy, automating schema transformations, and practicing vigilant testing and deprecation planning, you’ll keep your clients happy even as your API evolves. Ready to shield your users from breaking changes? Spin up that gateway, stitch in a field-mapping rule, and watch your endpoints handle version upgrades like a pro.